Securely authenticate to the AWS CLI with vaulted Access Keys
by Ricky White

The AWS CLI uses an access key to authenticate users to AWS services and perform various operations on cloud resources and workloads. An access key consists of an access key ID and a secret access key, which are used to sign the requests to the AWS servers. The access key ID identifies the IAM user or role making the request, and the secret access key is used to encrypt the request and verify the identity and permissions of the caller. If not adequately secured, however, an attacker can exploit these credentials to impersonate you, posing a severe security risk that can have devastating consequences for the key’s owner and users.
In this tutorial, you will learn the following:
- Why vaulting your AWS Access Key is crucial
- How to vault your AWS Access Key in a zero-knowledge vault
- How to config the AWS CLI to use Keeper’s Credential Process to retrieve the vaulted access key for secure authentication
Why Vault Access Keys?
A compromised AWS Access Key can allow an attacker to access and modify any AWS resources or services the key has permission to access, such as launching or terminating EC2 instances, creating or deleting S3 buckets, or invoking Lambda functions. Depending on the type and scope of the key, the cost of a compromised AWS Access Key can vary from financial losses, reputational damage, legal liabilities, and regulatory penalties.
By default, the AWS CLI uses credentials stored in plaintext in ~/.aws/credentials. These make the key susceptible to theft from malware and other endpoint compromise tactics. Being stored in plaintext means the key can be easily transmitted and stolen for nefarious use.
In this tutorial, you will use Keeper Securities secure Vault to store your AWS Access Key securely and the Keeper Secrets Manager (KSM) to programmatically access your secured Access Key to automate the authentication process for the AWS CLI.
Why use Keeper’s AWS CLI integration?
Keeper’s AWS CLI integration is what AWS refers to as a “Credential Process.” An AWS CLI credential process is a way to obtain credentials from an external source and use them with the AWS CLI and related tools.
In addition, Keeper’s AWS Credential Process is open source, which means you have visibility and transparency into the software components and their dependencies, ensuring your Software Bill of Materials (SBOM) is accurate. Any bugs and security updates are dealt with in the open, and you can view the source code and its development on GitHub. Please ‘star’ the project for notifications when new versions are released.
Securing your Access Key
As mentioned earlier, by default, the AWS CLI uses credentials stored in plaintext in ~/.aws/credentials. Once added to your Keeper Vault, you will remove the need to have them on disk and should delete them from your credentials file once secured.
There are two steps needed to secure your credentials and make them accessible. First, you will add your Access Key to the Keeper Vault.
Adding to the Vault
The first step in the integration setup is adding your AWS Access Key ID and Secret Access Key to a record in your Vault. There is no built-in record type for this kind of secret; however, you can create a custom record for AWS Access Keys and use that new template to create your record.
What you name this custom record type is up to you. However, the credential process looks for fields called Access Key ID and Secret Access Key. These fields must be present for successful authentication. Field names are case-sensitive, so you must ensure they match exactly.
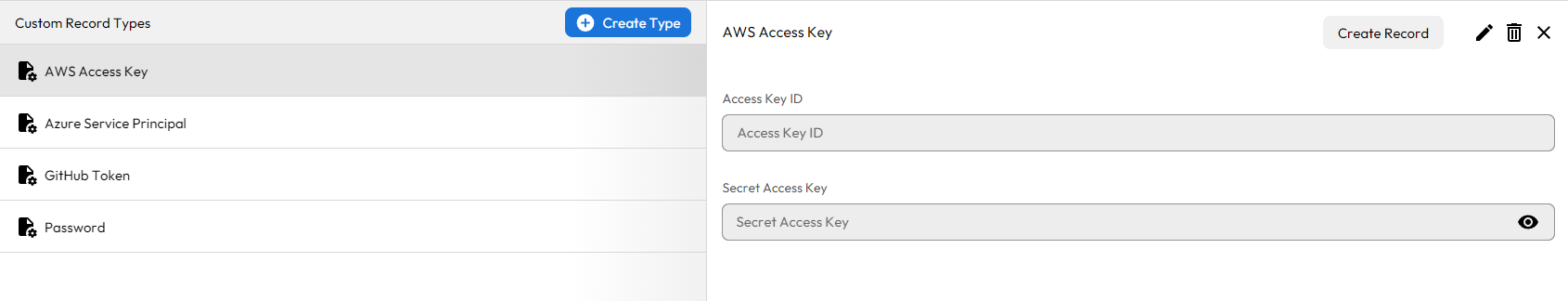
Now that your Access Key is vaulted, you must configure your KSM for the credential process.
KSM configuration
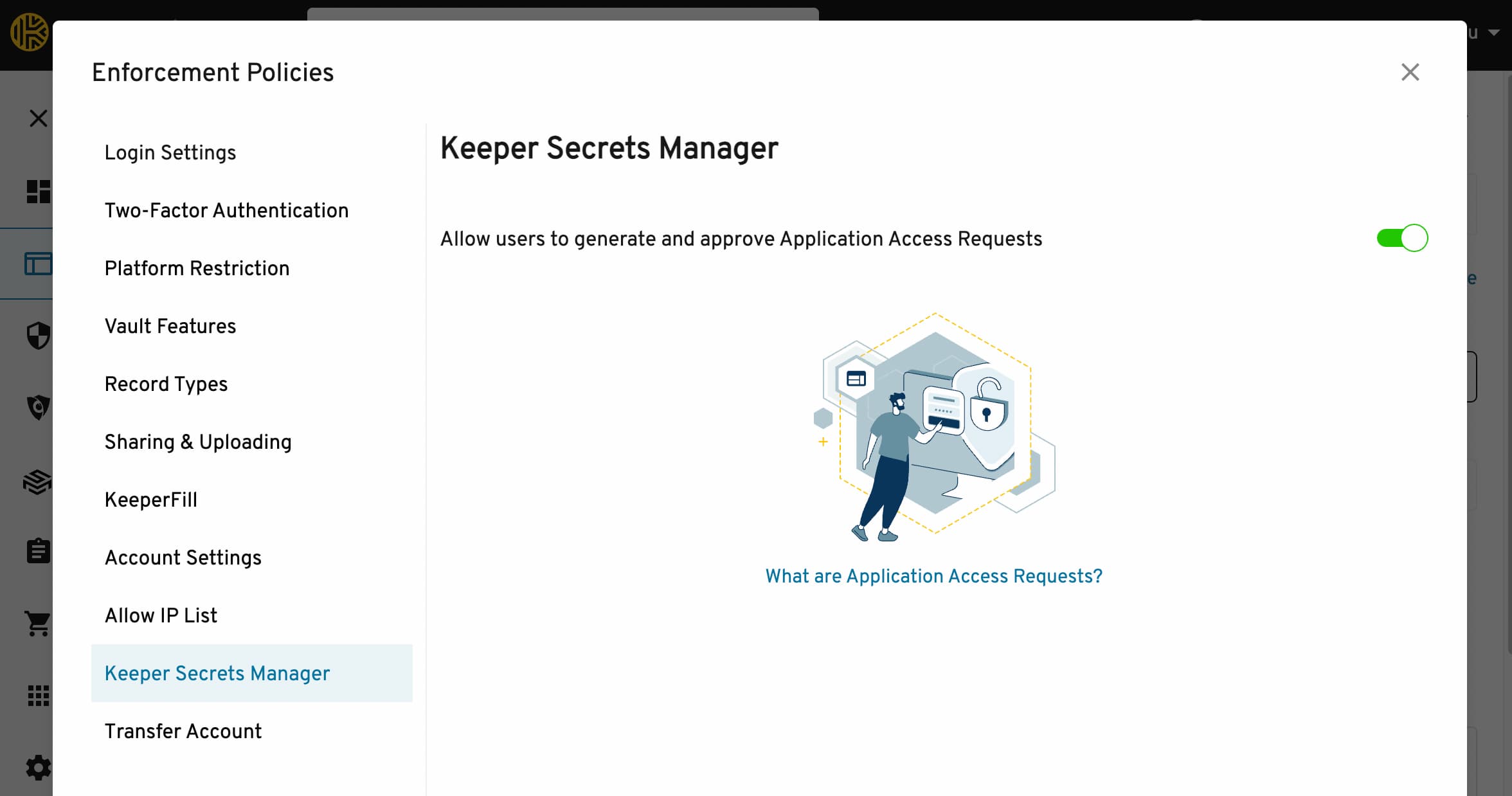
The credential process uses the zero-knowledge KSM provided by Keeper to fetch your Access Key from the vault. Therefore, you must ensure that:
- The KSM addon is enabled for your account
- You are assigned a role with the Secrets Management enforcement policy enabled .
Follow the linked documentation above for detailed instructions on setting up your account to access the KSM.
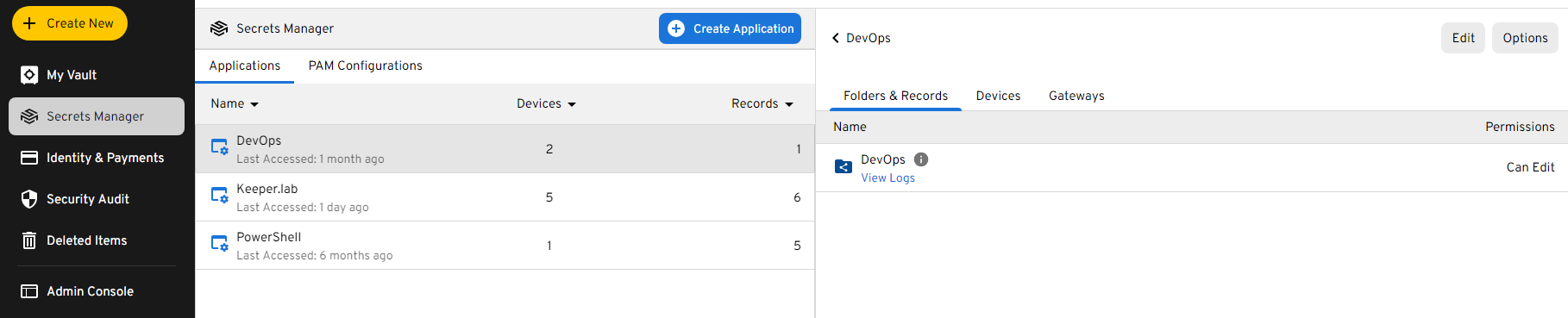
Once access to the KSM is available on your account, a Secrets Manager Application can be created. This Application will access the shared folder you created in which you stored your Access Key. The configuration file for the Application should be saved to .config/keeper/aws-credential-process.json relative to the user’s home directory for all systems. If this configuration is not found, the credential will check aws-credential-process.json relative to the user’s home directory as a backup. The integration currently only accepts the JSON format of the configuration.
You can find detailed instructions here to help set up your Secrets Manager Application and obtain your configuration file.
Now that you have your KSM configured and your AWS Access Key vaulted, the final step is configuring the AWS CLI.
AWS Config
Before amending your AWS config file, download the keeper-aws-credential-process executable from the GitHub releases page
and store that in a convenient location.
In your AWS configuration file, which is usually located at ~/.aws/config, add the following line to any profile you use via the CLI.
credential_process = /path/to/keeper-aws-credential-process --uid <Record UID>
The UID should be the record UID of the Access Key you wish to use to authenticate the AWS CLI. If you have multiple profiles set up in your AWS config, you can use a different Access Key for each profile using this integration for even better security.
Using the CLI
Once configured as above, the AWS CLI will automatically fetch your authentication credential from the Keeper Vault using the supplied UID. You can test that it works by using any CLI command in which you have an appropriate IAM role for, such as:
# List all s3 buckets
aws s3 ls
Congratulations, you are now fully set up if the command completes without error.
Anytime the CLI needs to reauthenticate you, it will be done automatically, as long as the record containing your Access Key remains available to the KSM and the UID does not change. You can change and add as many access keys to your vault as you require; just be sure to update your AWS configuration with the new or amended UID.
Conclusion
Vaulting your AWS Access Keys is a crucial security measure to protect your cloud resources and workloads. This tutorial explored the steps to securely store AWS credentials in Keeper’s zero-knowledge vault and configure the AWS CLI to authenticate using Keeper’s open-source credential process integration.
Key takeaways include:
- Storing AWS credentials in plaintext risks account compromise and should be avoided. Keeper’s vault provides robust security protections, including encryption, access controls, and visibility.
- The Keeper Secrets Manager enables programmatic and automated access to vaulted secrets for integrations like the AWS CLI. Proper configuration ensures your credentials remain secured even while in use.
- Keeper’s open-source credential process integration allows the AWS CLI to authenticate using your vaulted credentials without exposing the secrets, which is more secure than default methods.
- Multiple AWS Access Key credentials can be stored and used with different profiles for better security segmentation and access control.
By vaulting your keys and utilizing Keeper’s secure integrations, you can significantly reduce the risk of credential theft and account compromise when working with AWS services. This protects both your cloud environments and your organization’s security posture.
If you need assistance rolling this integration out to all your developers or want to see what Keeper Security can offer you regarding features and security compliance, get in touch.